Article Categories
- All Categories
-
 Data Structure
Data Structure
-
 Networking
Networking
-
 RDBMS
RDBMS
-
 Operating System
Operating System
-
 Java
Java
-
 MS Excel
MS Excel
-
 iOS
iOS
-
 HTML
HTML
-
 CSS
CSS
-
 Android
Android
-
 Python
Python
-
 C Programming
C Programming
-
 C++
C++
-
 C#
C#
-
 MongoDB
MongoDB
-
 MySQL
MySQL
-
 Javascript
Javascript
-
 PHP
PHP
How does communication happen between Manager & Agent?
The manager sends a request to an agent, and the agent responds to the request, known as Request/Response interaction. The request is usually used to retrieve or modify management information associated with the network device.
Requests which are generated by the manager can be as follows −
Get request-PDU − In this manager generates a request for requesting information on specific variables.
Get Bulk request Bulk − The manager generates a request for bulk information retrieval introduced in SNMP version 2. It allows the return of as much information as possible in a packet.
Set request PDU − It creates or modifies management information form the manager to set a value in a response generated by the agent.
Response PDU − Agent must always reply using response PDU.
Request/Response Interaction between one manager to other managers. One manager sends a request to another manager and the different response to the first one. The request is usually to notify another manager of MIB using the command Inform-Request PDU.
Unconfirmed interaction in which an agent sends Trap-PDU to request a manager. It is used to notify the manager of an exceptional situation due to which changes take place in management information associated with the network device.
The interaction between manager and Agent can be as shown in the figure below −
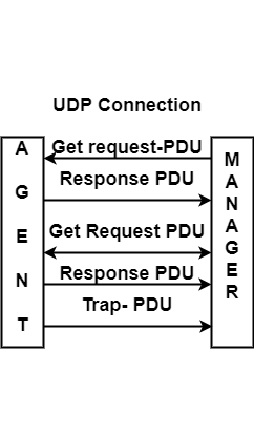
Get request PDU is a request issued by the manager that contains a unique request-id to match the request’s response, can be zero-valued error status or some variable binding.
The agent issues a response containing the same request-id, a zero-valued error status if an error or same variable binding. If the exception occurs for one or more variables, then the particular error status for each variable is sent.
In SNMP version 3, a complex framework for message exchange is used & also complicated for security & extensibility purposes. The security system contains a user-based security model. This model is intended to protect against unauthorized modification of information, protect from eavesdropping, denial of service etc.


