
 Data Structure
Data Structure Networking
Networking RDBMS
RDBMS Operating System
Operating System Java
Java MS Excel
MS Excel iOS
iOS HTML
HTML CSS
CSS Android
Android Python
Python C Programming
C Programming C++
C++ C#
C# MongoDB
MongoDB MySQL
MySQL Javascript
Javascript PHP
PHP
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
- Who is Who
Explain secure password Encryption with PowerShell.
Many times we need to use passwords in PowerShell and need to pass it to the credential parameter and a password should be always a secure string, not a plain text. There are few methods to encrypt the password as mentioned below.
a) Get-Credential Format
We have one method where we can store the username and password is through cmdlet Get-Credential. It will provide a GUI prompt. You can store this password into a variable and use it later in the command.
$cred = Get-Credential
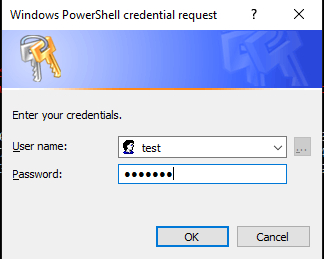
Credentials are stored into $cred variable. Here is the value of the variable. output below.
PS C:\WINDOWS\system32> $cred UserName Password -------- -------- test System.Security.SecureString
You can see the password is stored in the secure string. You can use the above variable with the credential parameter that cmdlet supports.
For example,
Invoke-Command -ComputerName Test-PC -ScriptBlock {Get-Service} -
Credential $cred
You can see how this password looks in encrypted form and for that, you need to use ConvertFrom-SecureString command.
PS C:\WINDOWS\system32> $cred.Password | ConvertFrom-SecureString 01000000d08c9ddf0115d1118c7a00c04fc297eb01000000fe83583138f0ce4bb0e3654f0529948100000000020000000000 106600000001000020000000cf8760de4e2ca7a28c8efd055c578dc7779f3984f25c1f9bc8c7a8ec50d97aa1000000000e80 00000002000020000000fb33efe90790e302ee738ad245b0b256d34e49728a08dfd2ef524da22f9bccaf100000003cf7a899 ea4c75edd7b4e418351f686040000000b21de677725588fb8f8bd589de058247171c103b48a50d06f152f25c8196935ca78f f7b1909bc5e76ad5c9cf1e2df497769aed3c1bb2f4035c26e6bdd7aa3875
b) Secure String Format
Another method to get the password in the secure string is to use the Read-Host command with –AsSecureString parameter.
PS C:\WINDOWS\system32> $passwd = Read-Host "Enter Password" -AsSecureString Enter Password: *******
You can use this password directly in the cmdlets that support the Credential parameter by creating a new PSCredential object as shown in the below example.
$username = Read-Host "Enter UserName" $passwd = Read-Host "Enter Password" -AsSecureString $creds = New-Object -TypeName System.Management.Automation.PSCredential -ArgumentList $username,$passwd Connect-VIServer -Server TestvCenter.lab -Credential $creds
When you check this password variable, it is also in the Secure.String format and again you can retrieve the encrypted password with ConvertFrom-SecureString pipeline command.
PS C:\WINDOWS\system32> $passwd System.Security.SecureString PS C:\WINDOWS\system32> $passwd | ConvertFrom-SecureString 01000000d08c9ddf0115d1118c7a00c04fc297eb01000000fe83583138f0ce4bb0e3654f05299481000000000200000000001 06600000001000020000000d5439c95404cc4e81dbb83b557e58cec12b5047e441b22bd3dabca96bc231d39000000000e8000 000002000020000000a9c2b95f3363ecbd46beaf927a1779ff2f43e17fb0e3aadf0d2c9c3dedc5fb1e10000000439a72d5bd9 97aacd529f49425909151400000008ad5e497b74e054e21ea1232c6ae45a64af302d91df09c0768eacd57b08f6b86f9bc4244 75c2e14173edd287e8a9304c570104475d09ebd9ab4c419167222260
Once your password string is secured, you can use directly it for the password. You don’t need to get the encrypted password with ConvertFrom-SecureString. It is just to see the password secure string.
c) Clear text format
What if the password is in the clear text format, you can use the clear text password directly in the command which supports the Password parameter but the below method is not recommended as it is in the clear text format and it can cause a major security breach. See the example below.
Connect-VIServer -Server TestvCenter.lab -User "Testadmin" - Password "PowerShell"
You can convert the clear text password into a secure string format. This is useful when you have a password text file placed in a secure location and PowerShell need to use the password without cleartext. The process is shown below.
$passwd = "Test@123" | ConvertTo-SecureString -AsPlainText -Force
PS C:\WINDOWS\system32> $passwd System.Security.SecureString
Now our password is secured and we can use it as a password in our credential. Here, we are connecting vCenter server named TestvCenter.lab with $cred parameter.
$creds = New-Object -TypeName System.Management.Automation.PSCredential -ArgumentList “test”,$passwd Connect-VIServer -Server TestvCenter.lab -Credential $creds
You can see the encrypted password with the method below. It is in the text encoded format, not the original password.
PS C:\WINDOWS\system32> $passwd | ConvertFrom-SecureString 01000000d08c9ddf0115d1118c7a00c04fc297eb01000000fe83583138f0ce4bb0e3654f052994810000000002 0000000000106600000001000020000000358daf9fec158cf68ccf5e06bf0eb829953553f5e703df2ce0d97e8a 95f5761f000000000e8000000002000020000000cf65dea31f8f4082392f958cd836b22cff2b6d86c3ab29d235 2f56aa757300b520000000f9626238a73c899ebf61bd935651a8deb391e2615164779d461c679ad04bc1264000 00007050962ea9d8c67f051b9fcbdbee953dffa2cc2377905911814a8d87d3e7678914a3e0292cb24977767881 6391919c5518d6251a78f87b6efd990cb3eabe96e4
If you need to store this password in the file then you can use the above command.
PS C:\WINDOWS\system32> $passwd | ConvertFrom-SecureString | Out-File C:\Passwd.txt
But when you are retrieving back your password, you need to convert again to the Secure string format because the credential parameter only accepts the secure strings.
PS C:\WINDOWS\system32> $passwd = (Get-Content C:\Passwd.txt) | ConvertTo-SecureString
PS C:\WINDOWS\system32> $passwd System.Security.SecureString
You can use this password in the credential parameter of the supported cmdlets.

