
- Cryptography - Home
- Cryptography - Origin
- Cryptography - History
- Cryptography - Principles
- Cryptography - Applications
- Cryptography - Benefits & Drawbacks
- Cryptography - Modern Age
- Cryptography - Traditional Ciphers
- Cryptography - Need for Encryption
- Cryptography - Double Strength Encryption
- Cryptosystems
- Cryptosystems
- Cryptosystems - Components
- Attacks On Cryptosystem
- Cryptosystems - Rainbow table attack
- Cryptosystems - Dictionary attack
- Cryptosystems - Brute force attack
- Cryptosystems - Cryptanalysis Techniques
- Types of Cryptography
- Cryptosystems - Types
- Public Key Encryption
- Modern Symmetric Key Encryption
- Cryptography Hash functions
- Key Management
- Cryptosystems - Key Generation
- Cryptosystems - Key Storage
- Cryptosystems - Key Distribution
- Cryptosystems - Key Revocation
- Block Ciphers
- Cryptosystems - Stream Cipher
- Cryptography - Block Cipher
- Cryptography - Feistel Block Cipher
- Block Cipher Modes of Operation
- Block Cipher Modes of Operation
- Electronic Code Book (ECB) Mode
- Cipher Block Chaining (CBC) Mode
- Cipher Feedback (CFB) Mode
- Output Feedback (OFB) Mode
- Counter (CTR) Mode
- Classic Ciphers
- Cryptography - Reverse Cipher
- Cryptography - Caesar Cipher
- Cryptography - ROT13 Algorithm
- Cryptography - Transposition Cipher
- Cryptography - Encryption Transposition Cipher
- Cryptography - Decryption Transposition Cipher
- Cryptography - Multiplicative Cipher
- Cryptography - Affine Ciphers
- Cryptography - Simple Substitution Cipher
- Cryptography - Encryption of Simple Substitution Cipher
- Cryptography - Decryption of Simple Substitution Cipher
- Cryptography - Vigenere Cipher
- Cryptography - Implementing Vigenere Cipher
- Modern Ciphers
- Base64 Encoding & Decoding
- Cryptography - XOR Encryption
- Substitution techniques
- Cryptography - MonoAlphabetic Cipher
- Cryptography - Hacking Monoalphabetic Cipher
- Cryptography - Polyalphabetic Cipher
- Cryptography - Playfair Cipher
- Cryptography - Hill Cipher
- Polyalphabetic Ciphers
- Cryptography - One-Time Pad Cipher
- Implementation of One Time Pad Cipher
- Cryptography - Transposition Techniques
- Cryptography - Rail Fence Cipher
- Cryptography - Columnar Transposition
- Cryptography - Steganography
- Symmetric Algorithms
- Cryptography - Data Encryption
- Cryptography - Encryption Algorithms
- Cryptography - Data Encryption Standard
- Cryptography - Triple DES
- Cryptography - Double DES
- Advanced Encryption Standard
- Cryptography - AES Structure
- Cryptography - AES Transformation Function
- Cryptography - Substitute Bytes Transformation
- Cryptography - ShiftRows Transformation
- Cryptography - MixColumns Transformation
- Cryptography - AddRoundKey Transformation
- Cryptography - AES Key Expansion Algorithm
- Cryptography - Blowfish Algorithm
- Cryptography - SHA Algorithm
- Cryptography - RC4 Algorithm
- Cryptography - Camellia Encryption Algorithm
- Cryptography - ChaCha20 Encryption Algorithm
- Cryptography - CAST5 Encryption Algorithm
- Cryptography - SEED Encryption Algorithm
- Cryptography - SM4 Encryption Algorithm
- IDEA - International Data Encryption Algorithm
- Public Key (Asymmetric) Cryptography Algorithms
- Cryptography - RSA Algorithm
- Cryptography - RSA Encryption
- Cryptography - RSA Decryption
- Cryptography - Creating RSA Keys
- Cryptography - Hacking RSA Cipher
- Cryptography - ECDSA Algorithm
- Cryptography - DSA Algorithm
- Cryptography - Diffie-Hellman Algorithm
- Data Integrity in Cryptography
- Data Integrity in Cryptography
- Message Authentication
- Cryptography Digital signatures
- Public Key Infrastructure
- Hashing
- MD5 (Message Digest Algorithm 5)
- SHA-1 (Secure Hash Algorithm 1)
- SHA-256 (Secure Hash Algorithm 256-bit)
- SHA-512 (Secure Hash Algorithm 512-bit)
- SHA-3 (Secure Hash Algorithm 3)
- Hashing Passwords
- Bcrypt Hashing Module
- Modern Cryptography
- Quantum Cryptography
- Post-Quantum Cryptography
- Cryptographic Protocols
- Cryptography - SSL/TLS Protocol
- Cryptography - SSH Protocol
- Cryptography - IPsec Protocol
- Cryptography - PGP Protocol
- Image & File Cryptography
- Cryptography - Image
- Cryptography - File
- Steganography - Image
- File Encryption and Decryption
- Cryptography - Encryption of files
- Cryptography - Decryption of files
- Cryptography in IoT
- IoT security challenges, Threats and Attacks
- Cryptographic Techniques for IoT Security
- Communication Protocols for IoT Devices
- Commonly Used Cryptography Techniques
- Custom Building Cryptography Algorithms (Hybrid Cryptography)
- Cloud Cryptography
- Quantum Cryptography
- DNA Cryptography
- One Time Password (OTP) algorithm in Cryptography
- Difference Between
- Cryptography - MD5 vs SHA1
- Cryptography - RSA vs DSA
- Cryptography - RSA vs Diffie-Hellman
- Cryptography vs Cryptology
- Cryptography - Cryptology vs Cryptanalysis
- Cryptography - Classical vs Quantum
- Cryptography vs Steganography
- Cryptography vs Encryption
- Cryptography vs Cyber Security
- Cryptography - Stream Cipher vs Block Cipher
- Cryptography - AES vs DES ciphers
- Cryptography - Symmetric vs Asymmetric
Cryptography - Transposition Techniques
The transposition technique is a kind of encryption that works by performing permutation on the given plaintext. Transposition ciphers are created by using the transposition technique to map normal text into ciphertext.
This chapter will cover multiple uses of the transposition technique as well as the variations between transposition and the substitution technique.
On the other hand, the substitution approach substitutes a symbol in plaintext with a symbol in ciphertext. However, the transposition method generates the ciphertext by applying permutation to the original plaintext.
Transposition Techniques
Rail Fence Transposition
Columnar Transposition
Columnar Transposition - Multiple Rounds
Book Cipher/Running Key Cipher
Vernam Cipher
Let us discuss these techniques one by one in the below sections −
Rail Fence Transposition
Rail-Fence is a basic Transposition method in which plaintext is written as a series of diagonals, which is then read row by row to generate the ciphertext.
Algorithm
Step 1: A series of diagonals is used to write the plaintext.
Step 2: The text is then read as a sequence of rows in order to extract the ciphertext.
To help you understand it, let me to give you an example.
Plaintext: Let us meet Today
We will now write this simple sentence in a diagonal format, as you can see below, following a specific order −
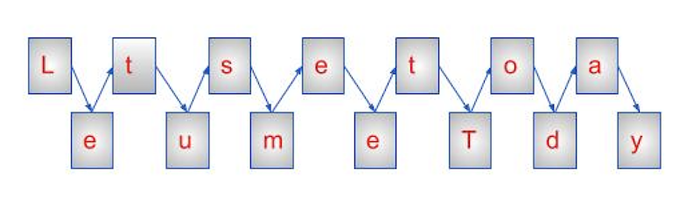
We can see why it was given the term "Rail Fence" by looking at the image, which actually looks like a rail fence.
After writing the message as a series of diagonals, you must read it as a series of rows in order to extract the ciphertext. Therefore, after reading the first row, the ciphertext's first half will be −
Ltsetoa
We will decipher the second part of the ciphertext by reading the second row of the Rail Fence −
eumeTdy
Now, we will add the two sides of the ciphertext together to get the full ciphertext, which is as follows −
Ciphertext: LTSETOAEUMETDY
The rail fence cipher is simple to use and even simpler to break for a cryptanalyst. Thus, a more complex method is required.
Columnar Transposition
In comparison to the rail fence, the columnar transposition cipher is more complex. To get ciphertext using this method, use these steps −
Algorithm
Step 1: The plain text is written in a row-by-row pattern in a rectangular matrix of the given size.
Step 2: To get the ciphertext, read the text from a rectangular matrix column by column. However, before reading the data column by column, you must first permute the column order. The received message is the ciphertext message.
To understand columnar transposition, consider this example −
Plain text: Let us meet Today
Place the plaintext in a predefined−size rectangle. In our case, the rectangle's defined size is 3x5. The image below shows plaintext placed in a 3x5 rectangle. Also, we permuted the column order.
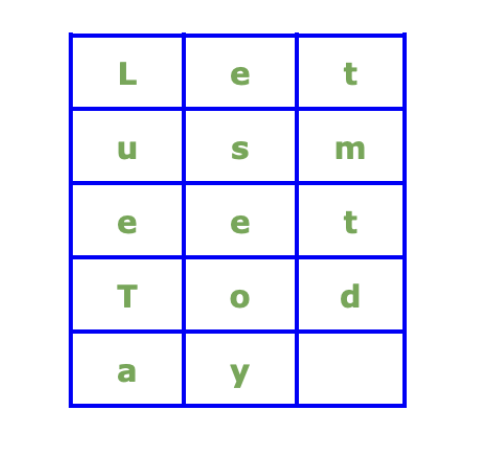
To get the ciphertext, we need to read the plaintext column by column in a permuted column order. So the ciphertext created using columnar transposition cipher is as follows −
Ciphertext: LUETAESEOYEMTD
Similar to the rail fence cipher, the columnar cipher can be easily broken. The cryptanalyst just needs to test a few permutations and combinations of the column order to obtain the permuted column order resulting in the original message. As a result, a more complicated method had to be used to secure the encryption.
Columnar Transposition - Multiple Rounds/ Improved Columnar Transposition
It is same as the simple columnar method but offers an improvement. This columnar method is applied to the plaintext more than once. The steps for using the columnar approach with multiple rounds are as follows −
Algorithm
Step 1: Plaintext is written in a predefined rectangle, row by row.
Step 2: To get the ciphertext, read the plaintext in the rectangle, column by column. Before reading the text in a rectangle column by column, rearrange the columns in the same manner as in the basic columnar technique.
Step 3: To produce the final ciphertext, repeat the steps above several times.
So now we will perform first round as per the above method and after first round the ciphertext will be as mentioned below −
Ciphertext: LUETAESEOYEMTD
To decipher the ciphertext for round 2, arrange the first round's ciphertext in a 3x5 rectangle and rearrange the columns. The extracted ciphertext for round 2 is LSYETMOATTEMUD. In this method, we can execute as many iterations as needed. Increasing the number of repetitions increases the complexity.
Book Cipher/Running Key Cipher
The book cipher, also known as the running key cipher, operates on the same basic principles as the one-time pad cipher. In onetime pad cipher, the key has the same length as the plaintext and is deleted after use. Every time a new key is used to send a new message.
The key or onetime pad is extracted from the book, which is an improvement over the onetime pad in Book Cipher. Let us outline the various stages −
Step 1: Convert plaintext to numeric form: A=0, B=1, C=3, ...Z=25.
Step 2: Take a one-time pad or key from any of the books and convert it to numeric format. But the key has to be the same length as the plain text.
Step 3: Now combine the numeric forms of plain text and key, matching each plaintext letter with the corresponding key text letter. If the sum of any plaintext letter and the matching key text letter exceeds 26, subtract 26.
Let us discuss this with an example −
Plain text: Meet tomorrow.
The key is from the book: ANENCRYPTION.
Now we have to turn this plaintext and key text into numeric form and combine them to get ciphertext, as seen in the image below −
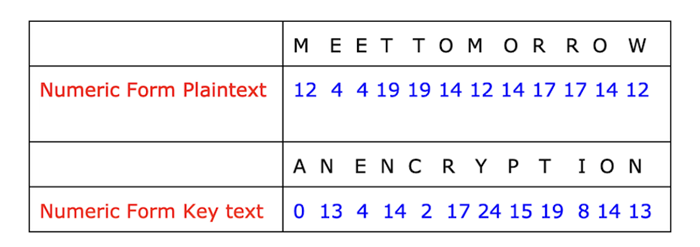
Add the numeric form of plaintext and key text. So after adding both the values we will get 12 7 8 32 21 31 36 29 36 25 28 35 −
Now we have some numbers in the above outcome (shown in bold) which is greater that 26 so we will subtract these number with 26 and then the final outcome will be − 12 17 8 6 21 5 10 3 10 25 3 9
So the new ciphertext will be: MRIGVFKDKZDJ.
Vernam Cipher
A one-time pad is a subset of the Vernam cipher that uses a random set of nonrepeating characters as its input ciphertext. The ciphertext used for transposition is never utilised for another message after it has been used. The input ciphertext's length needs to match the plain text's length.
Algorithm
Step 1: Put every character in the plaintext in numerical order, like A = 0, B = 1, ... Z = 25.
Step 2: Carry out step 1 again for every character in the input ciphertext.
Step 3: Increase the relevant input ciphertext character number by one for each number that's equivalent to a plaintext character.
Step 4: Subtract 26 from the total if it is higher than 25.
Step 5: Convert each sum's number into the appropriate character.
Step 6: A ciphertext is what step 5's output will be.
The Vernam cipher is only appropriate for brief messages since, after use, the input ciphertext cannot be used again.
For Example: The plaintext message is point and ciphertext is ntcba
| Plaintext | p | o | i | n | t |
|---|---|---|---|---|---|
| 15 | 14 | 8 | 13 | 19 | |
| Inner ciphertext | n | t | c | b | a |
| 13 | 19 | 2 | 1 | 0 | |
| Addition of plain text and input ciphertext | 27 | 33 | 10 | 14 | 19 |
| Subtract with 26 if greater than 26 | 1 | 6 | 10 | 14 | 19 |
| Ciphertext | b | g | k | o | t |
So, the ciphertext will be: bgkot.
So, that is all about the Transposition technique, which uses permutation to convert plaintext into ciphertext.