
- OAuth 2.0 - Home
- OAuth 2.0 - Overview
- OAuth 2.0 - Architecture
- OAuth 2.0 - Client Credentials
- Obtaining an Access Token
- Accessing a Protected Resource
- OAuth 2.0 - Extensibility
- OAuth 2.0 - IANA Considerations
- OAuth 2.0 Useful Resources
- OAuth 2.0 - Quick Guide
- OAuth 2.0 - Useful Resources
- OAuth 2.0 - Discussion
OAuth 2.0 - Architecture
In this chapter, we are going to discuss the architectural style of OAuth 2.0:
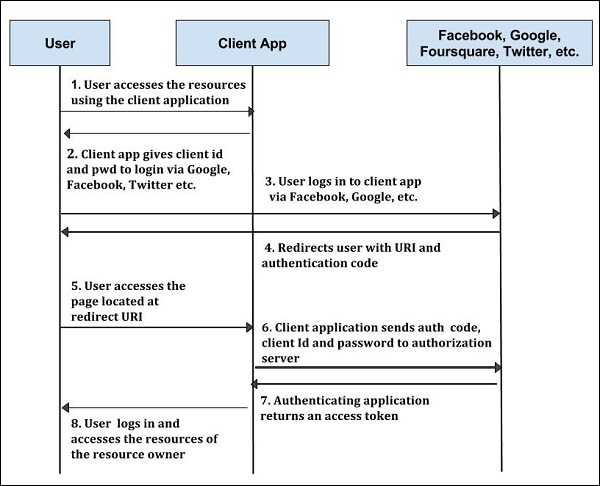
Step 1: First user accesses resources using the client application such as Google, Facebook, and Twitter etc.
Step 2: Next, client application will be provided with the client id and client password during registering the redirect URI (Uniform Resource Identifier).
Step 3: User logs using the authenticating application. The client ID and client password is unique to the client application on the authorization server.
Step 4: The authenticating server redirects the user to a redirect Uniform Resource Identifier (URI) using authorization code.
Step 5: Next user accesses the page located at redirect URI in the client application.
Step 6: Next, the client application will be provided with the authentication code, client id and client password and send them to the authorization server.
Step 7: Next, the authenticating application returns an access token to the client application.
Step 8: Once client application gets an access token, the user starts accessing the resources of the resource owner using the client application.
OAuth 2.0 has various concepts and are briefly explained in below table:
| S.N. | Concept & Description |
|---|---|
| 1 | Terminology OAuth provides some additional terms to understand the concepts of authorization. |
| 2 | Web Server Web server delivers the web pages and uses HTTP to serve the files that forms the web pages to users. |
| 3 | User-Agent User agent application is used by client applications in the user's device which acts as scripting language instance. |
| 4 | Native Application Native application can be used as instance of desktop or mobile phone application which uses the resource owner password credentials. |