
- SAP GRC Tutorial
- SAP GRC - Home
- SAP GRC - Overview
- SAP GRC - Navigation
- SAP GRC - Access Control
- Access Management Work Center
- Access & Authorization Mngmt
- SAP GRC - Authorization
- Access Control Launchpad
- Integration with Access Control
- SAP GRC - Integration with IAM
- SAP GRC - Audit Universe
- Process Control Work Centers
- SAP GRC - SoD Risk Management
- SAP GRC - Risk Management
- SAP GRC - Risk Remediation
- SAP GRC - Mitigation Controls
- SAP GRC - Superuser Privilege
- SAP GRC - Implementing Superuser
- SAP GRC - Enhanced Risk Analysis
- Assigning Mitigation Controls
- SAP GRC - Workflow Integration
- Installation and Configuration
- Data Sources and Business Rules
- SAP GRC - Creating Business Rules
- SAP GRC Useful Resources
- SAP GRC - Questions & Answers
- SAP GRC - Quick Guide
- SAP GRC - Useful Resources
- SAP GRC - Discussion
SAP GRC - Access Control
SAP GRC access control helps organizations to automatically detect, manage and prevent access risk violations and reduce unauthorized access to company data and information. Users can use automatic self-service to access request submission, workflow driven access request and approvals of access. Automatic reviews of user access, role authorization and risk violations can be used using SAP GRC Access Control.
SAP GRC Access Control handles key challenges by allowing business to manage access risk. It helps organizations to prevent unauthorized access by defining segregation of duties SoD and critical access and minimizing the time and cost of access risk management.
Key Features
The following are the key features of SAP GRC Access Control −
To perform audit and compliance as per legal requirements with different audit standards like SOX, BSI and ISO standards.
To automatically detect access risk violations across SAP and non-SAP systems in an organization.
As mentioned, it empowers users with self-service access submission, workflowdriven access requests and approvals of the request.
To automate reviews of user access, role authorizations, risk violations, and control assignments in a small and large scale organization.
To efficiently manage the super-user access and avoiding risk violations and unauthorized access to data and application in SAP and non-SAP system.
How to Explore Access Control Set Up Work Center?
Run the transaction for NWBC in SAP Easy access.
It will open NetWeaver Business Client screen and you will receive the following url − http://ep5crgrc.renterpserver.com:8070/nwbc/~launch/
Step 1 − To access Work Centers, open NetWeaver Business Client as mentioned above. Go to /nwbc option at the top to open Work Centers.
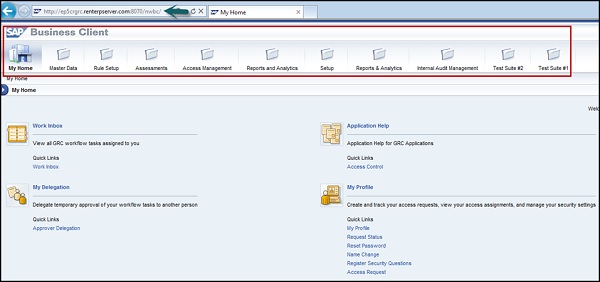
Step 2 − Once you click, you will be directed to the home screen of SAP NetWeaver Business client.
Step 3 − Go to setup work center and explore the work set. Click some of the links under each one and explore the various screens.
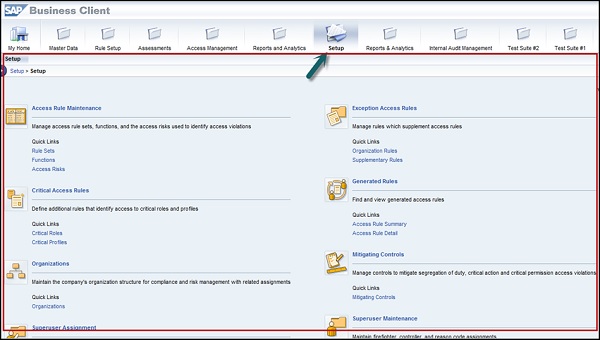
Step 4 − The Setup work center is available in Access Control and provides links to the following sections −
- Access Rule Maintenance
- Exception Access Rules
- Critical Access Rules
- Generated Rules
- Organizations
- Mitigating Controls
- Superuser Assignment
- Superuser Maintenance
- Access Owners
Step 5 − You can use the above listed functions in the following ways −
Using Access Rule Maintenance section, you can manage access rule sets, functions, and the access risks used to identify access violations.
Using Exception Access Rules, you can manage rules that supplement access rules.
Using critical access rules section, you can define additional rules that identify access to critical roles and profiles.
Using generated rules section, you can find and view generated access rules.
Under Organizations, you can maintain the company's organization structure for compliance and risk management with related assignments.
The Mitigating Controls section allows you to manage controls to mitigate segregation of duty, critical action, and critical permission access violations.
Superuser Assignment is where you assign owners to firefighter IDs and assign firefighter IDs to users.
Superuser Maintenance is where you maintain firefighter, controller, and reason code assignments.
Under Access Owners, you manage owner privileges for access management capabilities.