
- Network Security Tutorial
- Network Security - Home
- Network Security – Overview
- Network Security – Application Layer
- Network Security – Transport Layer
- Network Security – Network Layer
- Network Security – Data Link Layer
- Network Security – Access Control
- Network Security – Firewalls
- Network Security – Critical Necessity
- Network Security Useful Resources
- Network Security - Quick Guide
- Network Security - Useful Resources
- Network Security - Discussion
Network Security – Access Control
Network access control is a method of enhancing the security of a private organizational network by restricting the availability of network resources to endpoint devices that comply with the organization’s security policy. A typical network access control scheme comprises of two major components such as Restricted Access and Network Boundary Protection.
Restricted Access to the network devices is achieved through user authentication and authorization control which is responsible for identifying and authenticating different users to the network system. Authorization is the process of granting or denying specific access permissions to a protected resource.
Network Boundary Protection controls logical connectivity into and out of networks. For example, multiple firewalls can be deployed to prevent unauthorized access to the network systems. Also intrusion detection and prevention technologies can be deployed to defend against attacks from the Internet.
In this chapter, we will discuss the methods for user identification and authentication for network access followed by various types of firewalls and intrusion detection systems.
Securing Access to Network Devices
Restricting access to the devices on network is a very essential step for securing a network. Since network devices comprise of communication as well as computing equipment, compromising these can potentially bring down an entire network and its resources.
Paradoxically, many organizations ensure excellent security for their servers and applications but leave communicating network devices with rudimentary security.
An important aspect of network device security is access control and authorization. Many protocols have been developed to address these two requirements and enhance network security to higher levels.
User Authentication and Authorization
User authentication is necessary to control access to the network systems, in particular network infrastructure devices. Authentication has two aspects: general access authentication and functional authorization.
General access authentication is the method to control whether a particular user has “any” type of access right to the system he is trying to connect to. Usually, this kind of access is associated with the user having an “account” with that system. Authorization deals with individual user “rights”. For example, it decides what can a user do once authenticated; the user may be authorized to configure the device or only view the data.
User authentication depends up on factors that include something he knows (password), something he has (cryptographic token), or something he is (biometric). The use of more than one factor for identification and authentication provides the basis for Multifactor authentication.
Password Based Authentication
At a minimum level, all network devices should have username-password authentication. The password should be non-trivial (at least 10 character, mixed alphabets, numbers, and symbols).
In case of remote access by the user, a method should be used to ensure usernames and passwords are not passed in the clear over the network. Also, passwords should also be changed with some reasonable frequency.
Centralized Authentication Methods
Individual device based authentication system provides a basic access control measure. However, a centralized authentication method is considered more effective and efficient when the network has large number of devices with large numbers of users accessing these devices.
Traditionally, centralized authentication was used to solve problems faced in remote network access. In Remote Access Systems (RAS), the administration of users on the network devices is not practical. Placing all user information in all devices and then keeping that information up-to-date is an administrative nightmare.
Centralized authentication systems, such as RADIUS and Kerberos, solve this problem. These centralized methods allow user information to be stored and managed in one place. These systems can usually be seamlessly integrated with other user account management schemes such as Microsoft’s Active Directory or LDAP directories. Most RADIUS servers can communicate with other network devices in the normal RADIUS protocol and then securely access account information stored in the directories.
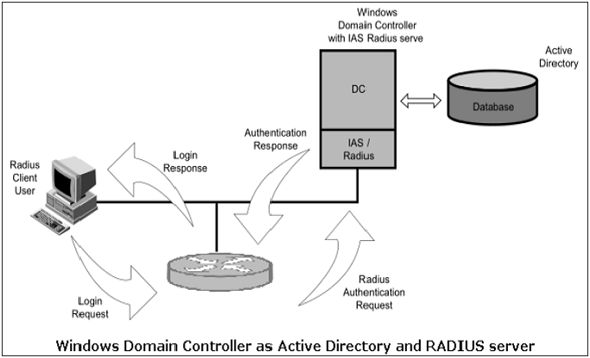
For example, Microsoft’s Internet Authentication Server (IAS) bridges RADIUS and Active Directory to provide centralized authentication for the users of devices. It also ensures that the user account information is unified with the Microsoft domain accounts. The above diagram shows a Windows Domain controller operating as both an Active Directory server and a RADIUS server for network elements to authenticate into an Active Directory domain.
Access Control Lists
Many network devices can be configured with access lists. These lists define hostnames or IP addresses that are authorized for accessing the device. It is typical, for instance, to restrict access to network equipment from IPs except for the network administrator.
This would then protect against any type of access that might be unauthorized. These types of access lists serve as an important last defense and can be quite powerful on some devices with different rules for different access protocols.