
- Mobile Security Tutorial
- Mobile Security - Home
- Mobile Security - Introduction
- Mobile Security - Attack Vectors
- App Stores & Issues
- Mobile Security - Mobile Spam
- Mobile Security - Android OS
- Mobile Security - Android Rooting
- Mobile Security - Android Devices
- Mobile Security - Android Tools
- Mobile Security - Apple iOS
- iOS Device Tracking Tools
- Windows Phone OS
- Mobile Security - BlackBerry OS
- Mobile Security - BlackBerry Devices
- Mobile Security - MDM Solution
- SMS Phishing Countermeasures
- Mobile Security - Protection Tools
- Mobile Security - Pen Testing
- Mobile Security Useful Resources
- Mobile Security - Quick Guide
- Mobile Security - Useful Resources
- Mobile Security - Discussion
Mobile Security - BlackBerry OS
BlackBerry OS is a proprietary mobile operating system developed by Research in Motion for its BlackBerry line of smartphones and handheld devices. It includes a Java based thirdparty application framework that implements J2ME Mobile Information Device Profile v2 (MIDP2) and Connected Limited Device Configuration (CLDC), as well as a number of RIM specific APIs.
Some of the features of BlackBerry include −
- Native support for corporate email
- BlackBerry enterprise server
- BlackBerry messenger
- BlackBerry internet service
- BlackBerry email client
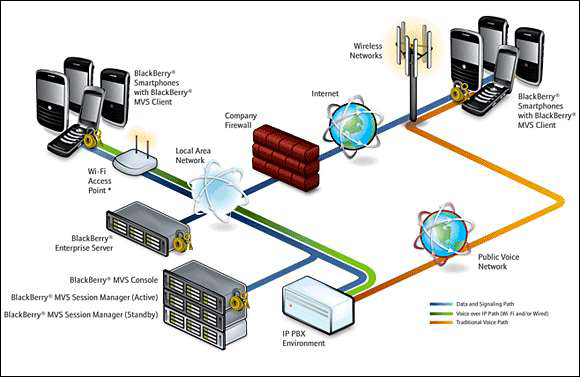
BlackBerry Enterprise Solution Architecture
Blackberry Enterprise Solution allows the mobile users to wirelessly access their organization emails and other business-critical applications, safely and securely. BlackBerry Enterprise Solution Architecture is comprised of six vital elements. They are −
- BlackBerry Enterprise Server
- Blackberry Mobile Data System
- BlackBerry Smartphones
- BlackBerry Connect Software
- Blackberry Alliance Program
- BlackBerry Solution Services
The enterprise server, together with enterprise messaging and collaboration systems, provides email access to the mobile users, enterprise instant messaging, and personal information management tools. Poorly configured firewalls increase the risk of attacks. The Web, Database, and Application Server contain vulnerabilities. If the attacker detects those vulnerabilities, then he or she can easily carry out an attack and take control over the entire server.
BlackBerry Attack Vectors
BlackBerry faces many attacks since there are many new tools and methods available for finding potential vulnerabilities present on BlackBerry devices. Attack vectors attract users to download malicious software on their mobiles. Finding website vulnerabilities using tools, etc. are the few techniques used by an attacker for carrying out attacks on BlackBerry devices. Apart from these techniques, there are many more attack vectors that allow attackers to launch attacks on BlackBerrys that include −
- Malicious Code Signing
- Memory and Processes Manipulations
- Email Exploits
- TCP/IP Connections Vulnerabilities
- Blackberry Malwares
- JAD File Exploits
- Short Message Service (SMS) Exploits
- PIM Data Attacks
- Telephony Attacks
Malicious Code Signing
A BlackBerry application must be signed by RIM to get full access to the operating system APIs. If a required signature is missing or the application is altered after signing, the JVM will either refuse/restrict the API access to the application or will fail at run-time with an error message. Attackers can obtain code-signing keys anonymously using prepaid credit cards and false details, sign a malicious application, and publish it on the BlackBerry app world. Attackers can also compromise a developer's system to steal code-signing keys and passwords to decrypt the encrypted keys.
JAD File Exploits and Memory/ Processes Manipulations
JAD files include the attributes of a Java application, such as app description and vendor details and size, and provides the URL where the application can be downloaded. It is used as a standard way to provide Over The Air (OTA) installation of Java applications on J2ME mobile devices. Attackers can use specially crafted .jad files with spoofed information and trick users into installing malicious apps.
Short Message Service (SMS) Exploits
Regular PC users are more likely to be targeted by premium rate dialers applications that connect a user's modem to a premium rate telephone number, which results in more service provider bills than expected. The same mechanism is enforced in BlackBerry but doesn't use premium rate SMSes.
Email Exploits
In BlackBerry mobile, all emails are sent, received, and read through the net.rim.blackberry.api.mail package and this package can be used only on signed applications. BlackBerry attachment service supports only files with extensions such as .doc, .pdf, .txt, .wpd,.xls, and .ppt, but it can send any kind of file via email. An attachment with file type .cod is not supported by BlackBerry.
PIM Data Attacks
Personal Information Management (PIM) data in the PIM database of a BlackBerry device includes address books, calendars, tasks, and memo pads information. Attackers can create malicious signed applications that read all the PIM data and send it to an attacker using different transport mechanisms. The malicious applications can also delete or modify the PIM data.
TCP/IP Connections Vulnerabilities
If the device firewall is off, signed apps can open TCP connections without the user being prompted. Malicious apps installed on the device can create a reverse connection with the attacker enabling him or her to utilize infected device as a TCP proxy and gaining access to organization's internal resources. Attackers can also exploit the reverse TCP connection for backdoors and perform various malicious information gathering attacks.