- Internet Security Tutorial
- Internet Security - Home
- Internet Security - Overview
- Internet Security - Cookies
- Internet Security - Phishing
- Internet Security - Social Network
- Internet Security - Chrome
- Internet Security - Mozilla
- Internet Security - Explorer
- Internet Security - Safari
- Internet Security - Gaming
- Internet Security - Child Safety
- Internet Security - Spamming
- Internet Security - Chatting
- Internet Security - File Download
- Internet Security - Transactions
- Internet Security - Banking
- Internet Security - e-Commerce
- Internet Security - Certificates
- Internet Security - Email Security
- Internet Security - Identity Theft
- Internet Security - Cybercrime
- Internet Security - Laws
- Internet Security - Checklist
- Internet Security Useful Resources
- Internet Security - Quick Guide
- Internet Security - Useful Resources
- Internet Security - Discussion
Internet Security - Transactions
Nowadays the security of the transactions are very important because these days most of the things are happening online.
The transactions happen in the following forms −
- When you go in a market and you use a POS for payment, then a transaction occurs.
- In your mobile phone when you download an android app to order something like the eBay app.
- When you pay something through an online payment service like paypal.com.
Check if You are Doing a Secure Transaction?
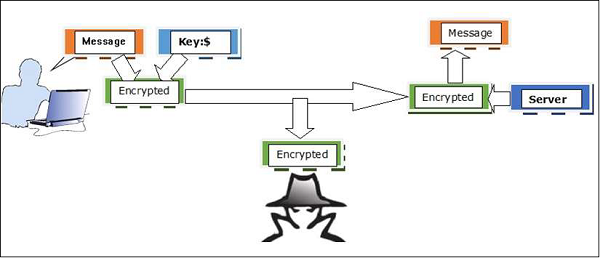
Generally a secure transaction happens in an encrypted form which happens between the site that we are connected to and the browser that we are using. It happens through a file in which the website provides its details, which we will deal further in the following sections. A simpler indication is recognizing the difference between a secure and insecure connection of which Https:// is a secured site, while Http:// is not secured.
If you or your users are using Google Chrome, you can push them to always connect securely, if the webpage supports it. Always prefer the HTTPS extension, if you are using a Mozilla Firefox there is an add-on called HTTPS Everywhere.
We should do a transaction only through webpages that we know or when they have a good reputation. So, in simple words you should visit those webpages that you trust and even though you trust, it is recommended to do the transactions through payment gateways like PayPal, so you don’t transmit bank account details to third parties.
A good resource is www.mywot.com that gives you the rates of the websites and their reputation based on millions of users, who trust their transaction to these websites.
At the end of the month always make a physical check of your transactions if they are matching to your expenditure or not. If it is not, then it is recommended to block your payment carts or accounts immediately.
After finishing the transactions, it is recommended that you always clear history, caches and cookies. Especially if you are using another computer that is not yours.
What Should You do as a System Administrator?
As a system administrator, you should have in mind some rules that will help our customers to make a secure transaction.
In the first place, you should check if there is any policy compliance for the system that we are offering, like PCI, or HIPAA. Generally, these policies have security guidelines too, like hardware or software that provides access controls, integrity controls, auditing and transmission security.
Another thing is that a session should be limited based on time and IP. So when your user signup form is getting the account open, the system will lock out after sometime and find out if there is a possibility of any man-in-the-middle attack. The IP restriction should not allow it.
Make a Usage Policy for your system, so the user knows their limit and gains knowledge regarding the security.
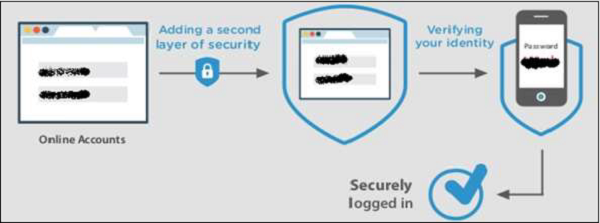
Check if your system has the proper configuration for making a financial transaction. The system should have a 2-factor authentication, where a passcode or a pin number is sent to your client’s mobile phone every time an online transaction takes place and will only be approved once you confirm the purchase by entering the code. This ensures that the client is who he says he is by asking for something he knows, and something he has, like a phone.