- Computer Security Tutorial
- Computer Security - Home
- Computer Security - Overview
- Computer Security - Elements
- Computer Security - Terminologies
- Computer Security - Layers
- Computer Security - Securing OS
- Computer Security - Antiviruses
- Computer Security - Malwares
- Computer Security - Encryption
- Computer Security - Data Backup
- Disaster Recovery
- Computer Security - Network
- Computer Security - Policies
- Computer Security - Checklist
- Legal Compliance
- Computer Security Useful Resources
- Computer Security - Quick Guide
- Computer Security - Resources
- Computer Security - Discussion
Computer Security - Layers
In Computer Security, layers is a well-known practice which was taken from military techniques. The aim of this is to exhaust the attacker when he succeeds to penetrate the first layer of security by finding a hole, then he has to find a hole in the second layer and so on, until he arrives at the destination if he succeeds.
Following is an image which explains about Layer Security.
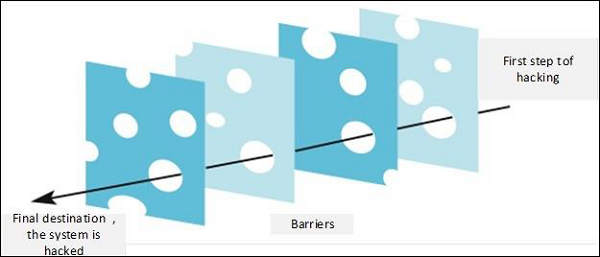
Let’s see the best practices in a Layer type of Security −
Computer Application Whitelistening − The idea is to install just a restricted number of applications in your computers, which are useful as well as are genuine.
Computer System Restore Solution − In case your computer is hacked and your files are damaged, you should have the possibility to again have access to your files. An example is Windows System Restore or Backup.
Computer and Network Authentication − The data that is accessed over the network is best to be provided only to the authorized users. Use usernames and passwords!!!
File, Disk and Removable Media Encryption − Generally a good practice is to encrypt hard disks or removable devices, the idea behind this is in case your laptop or your removable USB is stolen and it is plugged in another machine it cannot be read. A good tool for this is Truecrypt.
Remote Access Authentication − Systems which are accessed over the network is best to be provided only to the authorized users. Use usernames and passwords!!!
Network Folder Encryption − Again like the case of Network Authentication, if you have a network storage or a network folder shared, it is good to be encrypted to prevent any unauthorized user who is listening to the network to read the information.
Secure Boundary and End-To-End Messaging − Nowadays email or instant messaging is widely spread and it is the number one tool to communicate. It is better that the communication to be encrypted between the end users, a good tool for this is PGP Encryption Tool.