- Computer Security Tutorial
- Computer Security - Home
- Computer Security - Overview
- Computer Security - Elements
- Computer Security - Terminologies
- Computer Security - Layers
- Computer Security - Securing OS
- Computer Security - Antiviruses
- Computer Security - Malwares
- Computer Security - Encryption
- Computer Security - Data Backup
- Disaster Recovery
- Computer Security - Network
- Computer Security - Policies
- Computer Security - Checklist
- Legal Compliance
- Computer Security Useful Resources
- Computer Security - Quick Guide
- Computer Security - Resources
- Computer Security - Discussion
Computer Security - Elements
The general state in Computer Security has the ability to detect and prevent attacks and to be able to recover. If these attacks are successful as such then it has to contain the disruption of information and services and check if they are kept low or tolerable.
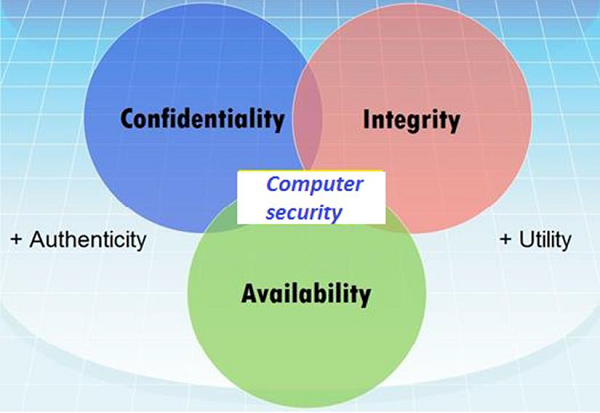
Different Elements in Computer Security
In order to fulfil these requirements, we come to the three main elements which are confidentiality, integrity, and availability and the recently added authenticity and utility.
Confidentiality
Confidentiality is the concealment of information or resources. Also, there is a need to keep information secret from other third parties that want to have access to it, so just the right people can access it.
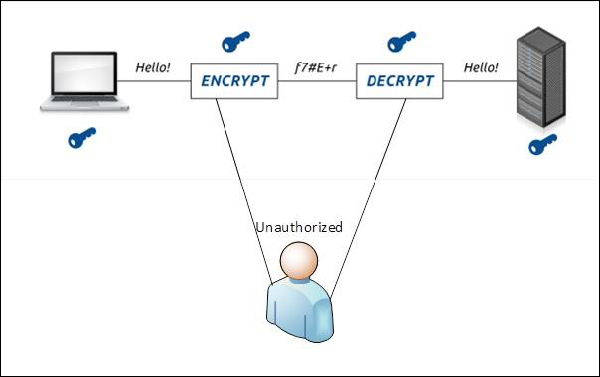
Example in real life − Let’s say there are two people communicating via an encrypted email they know the decryption keys of each other and they read the email by entering these keys into the email program. If someone else can read these decryption keys when they are entered into the program, then the confidentiality of that email is compromised.
Integrity
Integrity is the trustworthiness of data in the systems or resources by the point of view of preventing unauthorized and improper changes. Generally, Integrity is composed of two sub-elements – data-integrity, which it has to do with the content of the data and authentication which has to do with the origin of the data as such information has values only if it is correct.
Example in real life − Let’s say you are doing an online payment of 5 USD, but your information is tampered without your knowledge in a way by sending to the seller 500 USD, this would cost you too much.
In this case cryptography plays a very major role in ensuring data integrity. Commonly used methods to protect data integrity includes hashing the data you receive and comparing it with the hash of the original message. However, this means that the hash of the original data must be provided in a secure way.
Availability
Availability refers to the ability to access data of a resource when it is needed, as such the information has value only if the authorized people can access at right time. Denying access to data nowadays has become a common attack. Imagine a downtime of a live server how costly it can be.
Example in real life − Let’s say a hacker has compromised a webserver of a bank and put it down. You as an authenticated user want to do an e-banking transfer but it is impossible to access it, the undone transfer is a money lost for the bank.